OS4X Core - Updating OFTP2 certificate
Abstract
Sometimes it's necessary to update partner's or your certificate information due to several reasons:
- Expiration of certificate
- New certificate due to changed information
- Change of the used CA
- other reasons
In every case, you may change settings depending on some configuration situations. These are explained within this article.
Identify what to update
There are two major parts involved in certificates:
- TLS: Transport Layer Security. Offering a secure, encrypted TCP/IP connection, this mechanism is involved in server (and optionally: client) certificates, CRLs and trusted certificate information
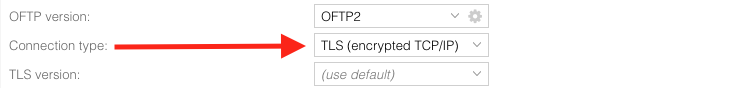
- OFTP2 security options: Using any of the OFTP2 options for secure authentification, file encryption, file signing or signed EERPs, you need to handle certificates per partner. Information like CRLs and trusted certificate are the basis for all operatione.
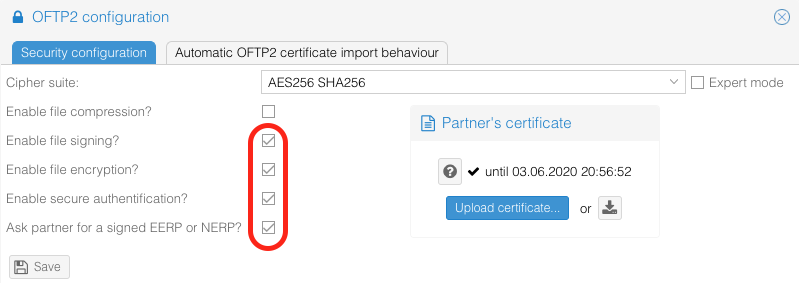
Basis for all secure operations are the trust of certificates. OS4X manages trust globally via the "trusted certificates", which are maintained in several ways:
- Automatically via TSL (a signed XML information hosted at Odette, containing a list of all trusted certificate authorities). Every OFTP2 system which is certified by Odette must be able to interpret this TSL, too.
- Manually via uploaded certificates in the "trusted certificates":
Trust at remote sites
We cannot guarantee how trust is managed in other implementations, so it depends on communication partner's software how they handle trust. It's possible that they handle it the same way, but it's not a technical specification how to implement it. Basically there are two options:
- They handle it the same way as OS4X does.
- The don't handle it the same way as OS4X does.
Depending on this information, and depending on what to update, there exist different approaches to update a certificate:
Update your own certificate at communication partner's side
When you obtain a new certificate, there may be steps depending on above selections:
- Usage as TLS certificate only (issued by a CA contained in Odette's TSL):
- Communication partner interprets TSL: no need for any interaction.
- Communication partner doesn't interpret TSL:
- Communication partner already has the CA chain of trust included in their system: send public certificate manually (i.e. via email, web download etc.)
- Communication partner doesn's have the CA chain of trust included in their system: send public certificate incl. chain of trust (meaning: all CA certificates up to the root certificate) to communication partner.
- Usage as TLS certificate (issued by a CA not included in Odette's TSL):
- Communication partner already has the CA chain of trust included in their system: send public certificate manually (i.e. via email, web download etc.)
- Communication partner doesn's have the CA chain of trust included in their system: send public certificate incl. chain of trust (meaning: all CA certificates up to the root certificate) to communication partner.
- Usage as certificate for OFTP2 security operations (and optionally as TSL certificate):
- Certificate is issued by a CA contained in TSL:
- Communication partner interprets TSL: Deliver new certificate as a substitution of the old certificate. This can also be done automatically via "OFTP2 certificate exchange".
- Communication partner doesn't interpret TSL: request how to continue manually.
- Certificate is issued by a CA contained in TSL:
Update partner's certificate
When you receive a certificate of a communication partner, inclusion into OS4X certificate pool relies on used security options:
- Usage as TSL certificate only:
- CA chain of certificate is contained in TSL (or uploaded manually in the past): no action required.
- CA chain of certificate is contained in not TSL (and not uploaded manually in the past): upload certificate chain into trusted certificated (possibly as PKCS7 container or every single certificate) minus the partner's certificate(!). The partner's certificate must not be included in the trusted certificates!
- Usage as certificate for OFTP2 security operations (and optionally as TSL certificate):
- If certificate is not issued by a CA included in the TSL (and CA path is not uploaded manually to "trusted certificates"): retrieve CA chain of trust, upload in trusted certificates manually.
- If certificate is not received via OFTP2's automatic certificate exchange: upload manually in partner's OFTP2 configuration