Difference between revisions of "OS4X Portal - internal daemons"
| Line 2: | Line 2: | ||
[[File:Bildschirmfoto 2019-04-08 um 14.13.20.png]] | [[File:Bildschirmfoto 2019-04-08 um 14.13.20.png]] | ||
| + | |||
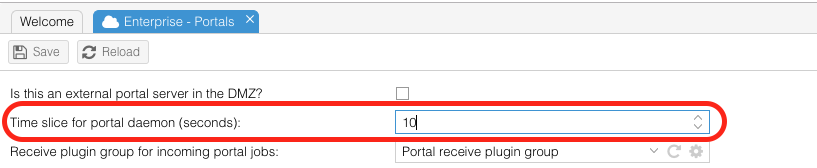
| + | All communication of the portal daemon to the DMZ is done via http(s). The configurable time slice in "Configuration" -> "OS4X Enterprise" -> "Portals" -> "Time slice for portal daemon (seconds)" has a direct impact on how fast all active OS4X Portal servers are contacted for new information. The result is a growing Apache access log: | ||
| + | |||
| + | [[File:Bildschirmfoto 2019-04-08 um 15.20.47.png]] | ||
[[Category:OS4X Portal]] | [[Category:OS4X Portal]] | ||
Latest revision as of 13:23, 8 April 2019
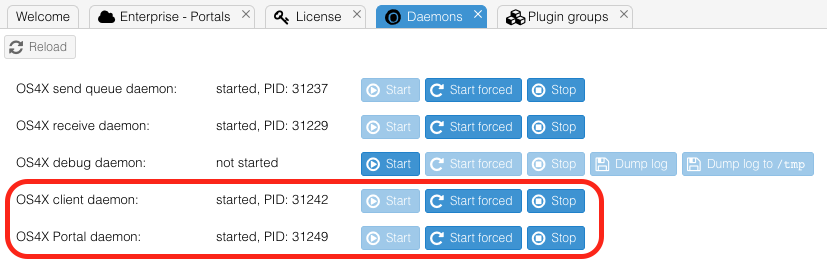
The internal zone of OS4X Portal consists of more daemons, offering more functionality. In addition to the known OS4X client daemon "os4xclientd", the OS4X Portal daemon is being used for the communication attempts from the internal to the external zone. It fetches all required information, events and jobs from the DMZ in order to process them as fast as possible to maintain data security in the DMZ. The OS4X Portal daemon is automatically started in the internal licensed zone with the runlevel script:
All communication of the portal daemon to the DMZ is done via http(s). The configurable time slice in "Configuration" -> "OS4X Enterprise" -> "Portals" -> "Time slice for portal daemon (seconds)" has a direct impact on how fast all active OS4X Portal servers are contacted for new information. The result is a growing Apache access log: