Difference between revisions of "OFTP2 information"
| Line 14: | Line 14: | ||
- or - | - or - | ||
*Elliptic curve Diffie–Hellman | *Elliptic curve Diffie–Hellman | ||
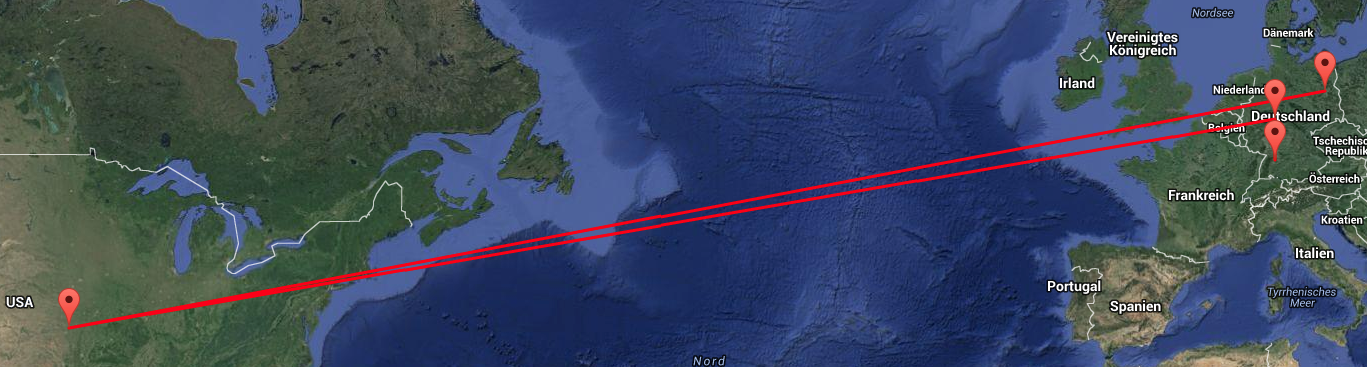
| − | your communication can be hijacked and decrypted offline, so all your information and data is | + | your communication can be hijacked and decrypted offline, so all your information and data is insecure. Have a look at the following map which show the TCP/IP traffic from southern germany to Berlin: it takes a route through the USA! |
[[Image:FirefoxScreenSnapz018.png]] | [[Image:FirefoxScreenSnapz018.png]] | ||
Revision as of 14:20, 4 April 2016
Logjam
When communicating with an OFTP2 TLS server which is not offering a secure Diffie-Hellman key exchange, the following log message will occure if you are using an actual OS4X version:
Why does this happen after updating to a recent version of OS4X?
The situation has been rised since May 2015, when the Logjam attack became public. As a result, the minimum requirement for Diffie-Hellman keys in the TLS handshake has been rised to 768bits (valid until end-2015) up to 1024bits (since Janiuary 2016).
We are very keen about our objective to transmit files securely over the internet, and we cannot leave security behind just for cosmetic reasons. We live online security, so we want that our customers profit from a secure communication product.
In real-life situation, what is happening here?
If your system does not use a TLS cipher with
- Diffie-Hellman key exchange with a key size of at least 1024bits
- or -
- Elliptic curve Diffie–Hellman
your communication can be hijacked and decrypted offline, so all your information and data is insecure. Have a look at the following map which show the TCP/IP traffic from southern germany to Berlin: it takes a route through the USA!
You may check your IP communication with traceroutes, resolve the hop IPs to geolocations and you'll get an impression about where your data packages are hijackable.
Solutions
There are several ways to overcome this situation:
Best solution: your communication partner offers a Diffie-Hellman key in the TLS handshake of appropriate size, actually more than 1024bits.
If the remote server uses a Diffie-Hellman key of at least 1024bits in size, you're actually safe and your communication cannot be decrypted as it is possible with a smaller key size. Perhaps the minimum value will rise in the future, so it's best to ask your partner for 1024bit and 2048bit DH keys.
Your communication partner offers a TLS cipher with Elliptic Curve Diffie-Hellman key exchange, which is not affected by this situation
On your own risk: you disable all ciphers using Diffie-Hellman key exchange
Use this option by activating the configuration parameter "Configuration" -> "TLS" -> "Allow insecure downgrade of TLS cipher". You will be asked for the CVE number of the Logjam attack, so you need to learn about this situation in order to better decide if this solution is what you want.