OS4X Core - Request a c-works OFTP2 certificate
In order to communicate OFTP2 partners, you need an OFTP2 certificate. As a customer using OS4X, you're able to request a full-trusted OFTP2 certificate for free. This documentation describes the steps to be made for a successful request and configuration procedure.
Requirement
- Your webserver (PHP) is able to communicate to the internet via https
- either directly
- or via a configured HTTP proxy
If no communication is possible, you can manually download the CSR and send it to us via eMail to support@os4x.com, but the most common way is the direct communication.
Request certificate
In order to obtain a certificate, you have to issue a request which will be encrypted using your own private RSA key. This procedure is fully automated in the OS4X administrative web interface, so you need no knowledge about commandline or other tools in order to create a RSA private key, create a CSR manually, extend special fields etc.
Navigate to the administrative web interface, go to "Certificates" -> "Cert. requests":
Then, click on "New CSR":
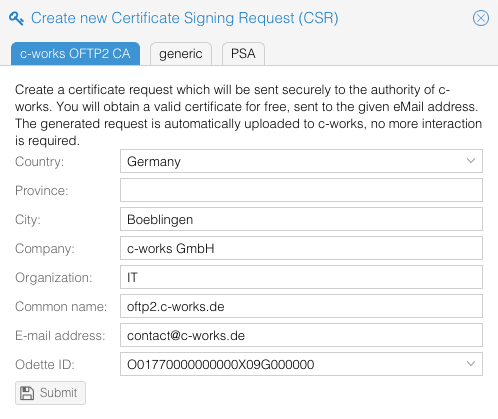
In the new opened panel, the tab "c-works OFTP2 CA" is pre-selected. Enter here your details of your OFTP2 contact. Special values are:
- Common name: normally, this is the DNS name of your OFTP2 system, reachable and resolvable from external internet, such as oftp2.company.com as an example.
- eMail address: this mail address will be used for later communication about the certificate, so it must exist. It's common to use an abstracted eMail address such as "oftp2@company.com" or other similar values.
- Odette ID: Your default Odette ID (as configured in "Configuration" -> "Odette") is entered here. Many communication partners rely on the correctness of that information.
Submit the certificate request when you have entered all values correctly. If you have mis-entered a value, just send an eMail to contact@os4x.com in order to let the request be deleted at no cost.
After having submitted the request, you receive (hopefully) an information:
CSR submitted
When your submitted CSR is waiting for approval, you have a white (non-green) line in your CSR panel where you can extract information like the CSR itself, take a look or download the private key etc.:
The icons on the left have the following meaning:
- Display the CSR itself in a human-readable way.
- Save the request as a file, in order to transfer it to a certificate authority on your own.
- (dimmed out; inactive as long as the line is not green): Download the certificate incl. private key as a file in PEM format. Keep this file secret!
- (dimmed out; inactive as long as the line is not green): Download the certificate excl. private key as a file in PEM format. You can transfer this file to any communication partner you want.
- (dimmed out; inactive as long as the line is not green): Use this issued certificate for several tasks. You will configure your TLS server and client with this option, also you're able to configure single or multiple or all partners with this certificate.
- Delete the request itself.
Receiving certificate
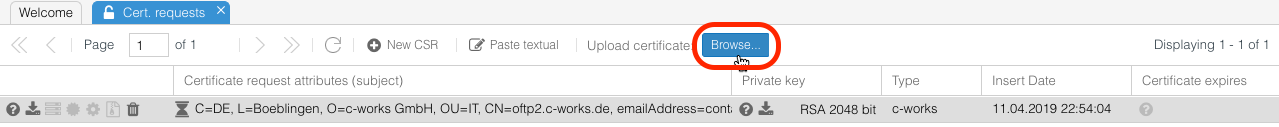
You will receive your certificate via eMail, addressed to the eMail address in the request field "eMail address". As an attachement, the certificate file will be contained. Upload the certificate file in the CSR panel via the "Upload certificate" button:
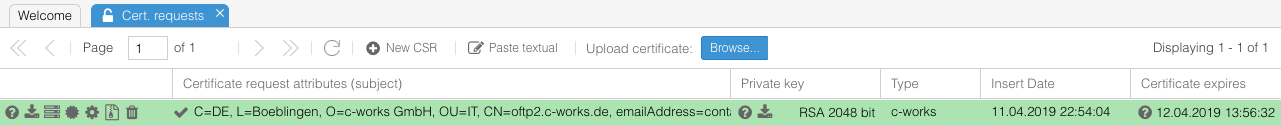
Your line of the corresponding certificate request will instantly turn green:
Use the certificate
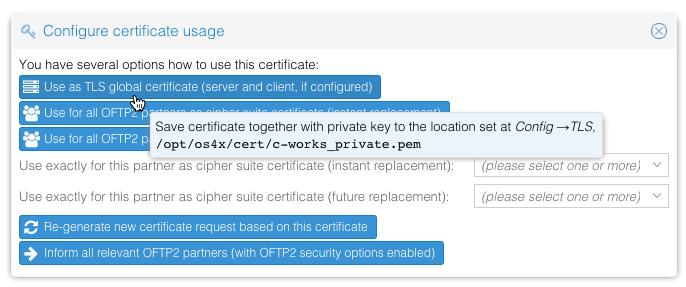
With a green line, you can use this issued certificate (in combination with your private key) for any security operation in OFTP2. To ease up the configuration, click on the 5th icon on the left labeled with "Use certificate...". A new panel opens:
If your configured OFTP2 TLS server certificate is writable by the webserver, you can easily write a new version of that file. A backup of the old file will be made, if possible (give the webserver write permissions to the directory where the certificate file is configured to). Afterwards, restart your OS4X daemons in order to activate the new certificate (active transfers are not affected).
If you have OFTP2 security enabled (secure authentification, file encryption, file signing or signed EERPs) for all, some or even one partner, you can use the buttons and comboboxes below in order to activate this certificate as an instant or future replacement of your current configuration. The certificate will then be saved in the partner's configuration and the partner is being informed by this change with an Odette OFTP2 certificate exchange mechanism.